#Multi Factor Authentication Tools
Explore tagged Tumblr posts
Text
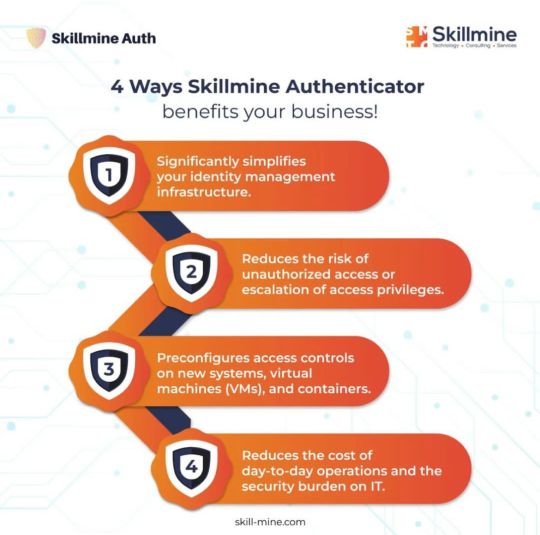
4 ways Skillmine Authenticator benefits your business!
Authenticator removes the need for users to remember, and manage multiple passwords. It centralizes authentication and simplifies access management across multiple applications in an organization. Auth supports various protocols and supports different social media platforms like Facebook, and Google. It also supports classical logins and fewer passwords logins.
1 note
·
View note
Note
Kunsel says:
We should maybe have a stricter definition of what counts as "hacking", okay?
It was a slow day at work, and he decided to guess people's email passwords in 10 attempts.
How does it go?
YESSSSSSSSS
Pro tips: make your password long, that is the most important factor. Use a password manager, most of them have a free option. Adding complexity does help, but focus on length first. Size does matter here. Multi-factor authentication (MFA) also helps a lot.
---------
Kunsel: Zack, gimme your password!
Zack: ...
Kunsel: Come on man, I need it for something!
Zack: 😭😭😭 buddy I would, but I forgot it again 😭😭😭😭😭😭
Kunsel: Ok man, it's ok, let's look around your desk...here, under this pile of chip bags, I think i saw...yeah, here's the penguin toy...and yep, Password Penguin has "Zack'ss00p3rp4ssw0rd!" written on the bottom. Let's try it!
(it works)
Zack: THANK YOU KUNSEL I THOUGHT I'D LOST HIM AND I COULDN'T REMEMBER AND-
Kunsel: *wheeze* Zack let go, I need to breathe *wheeze*

-----------
Kunsel tries to guess Roche's by typing it in.
M0t0rcycle!
ShinyDancer
Sh1n33D4nc3r!
He's in.

------------
Kunsel tries to guess Sephiroth's. On the 9th try, he gets it: Seph+Jenova4ever
Horrible things are uncovered along the way and now he needs to send Sephiroth some information very discreetly.
------------
Lazard. Kunsel knows better. He gives a few guesses, but decides to actually hack this.
He sets up a hash capturing tool over the internal network and waits for Lazard to log on. He does. Kunsel captures the hash and starts cracking it.
Three days later, the hash cracker has not worked and he has to give up on that.
Kunsel: Sir, I need to get into your email, will you please send me your password?
Lazard: Of course not, that is unsafe and against company policy. However, you're welcome to come to my office to perform any actions we both deem necessary.
Kunsel goes over and Lazard is using multifactor authentication, so just having the hash cracked wouldn't have worked anyway. He sets up a keylogger surreptitiously on Lazard's workstation while "performing updates" and showing Lazard new features in his email.
The things he captures with that keylogger:
* Numerous emails covering for boneheaded shit the SOLDIERs did.
* The letter "A" typed about a thousand times into a text file labeled "definitely not screams.txt".
* Moogle searches for "how to convince your employees to get therapy", "pasta recipes", "therapists near me", "child psychology for adults", "play therapy for adults", "cat psychology", and "shrimp pasta recipes".
* The password: &oh'ihiy_-8_gi"it"gi_ipkb0(-ur#3-@--LXS4ever--9(9;0(!08(098+pihjboigig(@ukopih

Then it is a simple matter of finding a zero-day race condition hack in the MFA software, timing things just right, and entering the password and hacked MFA key at the perfect moment.
Kunsel of course has pity on the man after seeing even more emails such as...
* Explaining to Roche that doing squats over his motorcycle makes it look like he's humping it, and it is making people uncomfortable.
* Asking Genesis to please not actually firaga the recruits this week, they don't need a lawsuit. No, it's not character building. No, even though it was part of his home training and Shinra sanctioned training a few years ago.
* Inviting Sephiroth over for shrimp pasta to discuss strategy.
* Asking Angeal to seek therapy so the others will follow his lead.
* Telling Zack that he could not have a therapy flamingo in the office. Even if it was a lawn ornament.
* Warning Hojo not to take Sephiroth this week.
* Warning Hollander not to take Genesis and Angeal this week.
* Reaming Heidegger out very politely for all his BS.
Kunsel logs out without doing anything. Lazard needs a break.

--------
Kunsel calls Angeal pretending to be the help desk. Angeal, a bit embarrassed over his upbringing and unsure because he feels unused to technology, eventually gives Kunsel the password: BanoraBoys123!

----------
Genesis' is guessed on the 7th try because Kunsel didn't want to bother typing in an entire stanza of Loveless with numbers instead of vowels.
1nf1n1t3_1n_myst3ry_1s_th3_g1ft_0f_th3_g0dd3ss__w3_s33k_1t_th7s_4nd_t4k3_t0_th3_sky_r1ppl3s...
He sends an email from Genesis inviting everyone to a Loveless recital on Tuesday. It backfires because several people, including Genesis, show up and have a great time.

-----------
Kunsel tries Zack's little trooper friend next. He's a tough nut to crack. He won't pick up his PHS to get vished, won't click on Kunsel's phishing emails, and won't tell Zack or Kunsel his password.
Kunsel captures his hash and cracks it. It takes a full 24 hours, but he gets it in the end:
!1986fuck_this_shit

#ff7#sephiroth#zack fair#cloud strife#genesis rhapsodos#angeal hewley#lazard deusericus#die hojo die#kunsel#hackerman kunsel
37 notes
·
View notes
Text
About Exnori

Hello, I am Exnori.com, a premier cryptocurrency exchange dedicated to revolutionizing the way you trade digital assets. I am here to offer a secure, efficient, and user-friendly platform that caters to both beginners and seasoned traders alike. Let me take you through the various aspects of my services and why I am the go-to choice for cryptocurrency trading.
Mission and Vision
At my core, my mission is to create a transparent, secure, and seamless trading environment. I strive to empower my users with the tools and knowledge they need to navigate the volatile world of cryptocurrencies confidently. My vision is to become a cornerstone of the cryptocurrency ecosystem, where traders can thrive and reach their financial goals.
Robust Security Protocols
Security is my utmost priority. I employ state-of-the-art encryption techniques, robust multi-factor authentication, and continuous monitoring to protect your assets and personal information. My security infrastructure is designed to be resilient against cyber threats, ensuring that your investments are safe with me.
User-Centric Design
I am designed with the user in mind. My platform boasts a clean, intuitive interface that simplifies the trading process. Whether you are accessing me via desktop or mobile, you will find a consistent and user-friendly experience that makes trading easy and accessible, no matter where you are.
Extensive Cryptocurrency Selection
I offer a vast selection of cryptocurrencies for trading. From established giants like Bitcoin, Ethereum, and Ripple to promising new altcoins, my diverse range of assets ensures that you can find the right opportunities to diversify your portfolio and maximize your trading potential.
Competitive and Transparent Fee Structure
I believe in providing value to my users. My fee structure is transparent and competitive, allowing you to understand exactly what you are paying for each transaction. By keeping fees low, I help you maximize your returns and make the most out of your trading activities.
Comprehensive Educational Resources
Knowledge is power, especially in the dynamic world of cryptocurrency. I offer a wealth of educational resources, including in-depth articles, video tutorials, and live webinars. These resources are tailored to help you understand market trends, develop effective trading strategies, and make informed decisions.
Advanced Trading Tools
For the more experienced traders, I provide a suite of advanced trading tools. These include detailed charting capabilities, technical indicators, and algorithmic trading support through my API. Whether you are a day trader or a long-term investor, my tools are designed to enhance your trading strategy and performance.
Community and Customer Support
I pride myself on fostering a vibrant community of traders. My platform encourages interaction and the exchange of ideas among users, creating a collaborative environment. Additionally, my customer support team is available 24/7 to assist you with any issues or questions you may have, ensuring a smooth and supportive trading experience.
Innovation and Continuous Improvement
The cryptocurrency market is constantly evolving, and so am I. I am committed to continuous innovation and regularly update my platform with new features and improvements. This dedication to staying ahead of the curve ensures that I can provide you with the best tools and technologies for successful trading.
Conclusion
Choosing Exnori.com means partnering with a platform that is dedicated to your success. With my robust security measures, user-centric design, extensive asset selection, competitive fees, and unwavering support, I am here to help you achieve your trading goals. Join me at Exnori.com and experience the future of cryptocurrency trading.
By joining Exnori.com, you are becoming part of a dynamic and forward-thinking community. Let's trade smarter, safer, and more effectively together. Welcome to Exnori.com, where your trading journey begins!
13 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
Federal Reserve Governor Michael Barr is urging banks to begin collecting behavioral and biometric data from customers to combat deepfake digital content created through ID. These deepfakes are capable of replicating a person’s identity, which “has the potential to supercharge identity fraud,” Barr warned.
“In the past, a skilled forger could pass a bad check by replicating a person’s signature. Now, advances in AI can do much more damage by replicating a person’s entire identity,” Barr said of deepfakes, which have the “potential to supercharge identity fraud.”
“[We] should take steps to lessen the impact of attacks by making successful breaches less likely, while making each attack more resource-intensive for the attacker,” Barr insists, believing that regulators should implement their own AI tools to “enhance our ability to monitor and detect patterns of fraudulent activity at regulated institutions in real time,” he said. This could help provide early warnings to affected institutions and broader industry participants, as well as to protect our own systems.”
Enabling multi-factor authentication and monitoring abnormal payments is a first step, but Barr and others believe that banks must begin to collect their customer’s biometric data. “To the extent deepfakes increase, bank identity verification processes should evolve in kind to include AI-powered advances such as facial recognition, voice analysis, and behavioral biometrics to detect potential deepfakes,” Barr noted.
Barr would like banks to begin sharing data to combat fraud. Deepfake attacks have been on the rise, with one in 10 companies reporting an attack according to a 2024 Business.com survey. Yet, will our data be safer in the hands of regulators?
2 notes
·
View notes
Text
How do businesses use Microsoft technologies?
Microsoft Technologies Services

In today’s fast-paced and modern digital world, businesses rely on powerful tools and resources to stay productive, secure, and competitive. Microsoft Technologies provides many solutions that help organizations streamline operations, improve communication, and grow efficiently. Companies across all industries, from small startups to large enterprises, use Microsoft tools to power their success.
Enhancing Team Collaboration and Productivity -
One of the most common uses of Microsoft Technologies is to improve how teams work together. Microsoft 365 tools like Outlook, Teams, SharePoint, and OneDrive make it easy for employees to share files, hold virtual meetings, and manage tasks in real time—no matter where they are.
Cloud Computing with Microsoft Azure -
Businesses use Microsoft Azure to host websites, applications, and databases in the cloud. Azure allows companies to scale their IT resources and tools up or down based on the objective demand, which lower costs and increases flexibility. It also supports data backup, disaster recovery, and AI-driven services.
Managing Customer Relationships -
Microsoft Dynamics 365, resources assists the companies to handle out their sales, customer service, and marketing in one place at a time. With insights powered by data and automation, businesses can build stronger customer relationships and make smarter decisions faster with the assistance of Microsoft Technologies.
Improving Security and Compliance -
With cyber threats on the rise, Microsoft Technologies offers built-in security tools to help protect sensitive data. Features like multi-factor authentication, data encryption, and compliance tracking help businesses meet industry regulations and secure their systems.
Automating Processes with Power Platform -
Tools like Power Automate and Power Apps allow businesses to create custom apps and automate repetitive tasks without writing complex code. This helps save time and lets employees focus on more important work.
Businesses use Microsoft Technologies to stay efficient, connected, and secure in a digital-first world. Whether through cloud computing, team collaboration tools, or business intelligence platforms, Microsoft remains a trusted partner for organizations looking to grow and succeed. Additionally, Microsoft and its tools support the organization with remote work offerings and hybrid environments setup, and digital transformation with ease. Their solutions helps out the businesses to stay agile and alert, adaptive to change quickly, and remain competitive in the ever-evolving market as leads towards stand out of the domain in the industry.
Partnering with Experts for Microsoft Technology -
Businesses can rely on shifting their existing system and operating structure to new mediums as if for Microsoft tools with companies and experts like Suma Soft, IBM, and Cyntexa for a hassle-free Microsoft rollout journey.
As these set of industry leaders and experts assure a smooth transition with custom solutions offerings with its adaptation into the system with advanced security measures, and ongoing support, allowing the companies to maximize the benefits of their modern digital infrastructure.
#it services#technology#saas#software#digital transformation#saas development company#saas technology
2 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Lifesaving Tech with Hidden Risks: Medical IoT Devices
Hey, so… what even are Medical IoT Devices?
Okay, let’s start with the basics. Medical IoT (Internet of Things) devices are basically smart gadgets that help doctors and patients manage health in real-time. Think of them as the Fitbits of the medical world, but way more advanced and sometimes implanted inside your body.
Here’s a quick rundown of the most common types:
Wearables: Smartwatches, glucose monitors, patches that track your vitals.
Implantables: Pacemakers, insulin pumps, neurostimulators that keep your heart ticking, your blood sugar in check, your brain functioning properly respectively.
Hospital Gear: Things like infusion pumps, ventilators, or MRI machines that are connected to the hospital’s network.
These devices are amazing because they can send data straight to your doctor, so they can monitor you without you having to camp out in a hospital bed. But (and there’s always a but), this connectivity comes with a price: security risks.
Wait, How Can a Pacemaker Get Hacked?
Okay, so let’s get into the nitty-gritty of how these devices can be exploited. It’s not just about “hackers being hackers”, there are specific technical flaws that make these devices vulnerable.
1. Encryption (or Lack Thereof)
Encryption is like a secret code that scrambles data so only authorized parties can read it. For medical IoT devices, encryption is crucial because they’re transmitting sensitive health data. But here’s the problem: not all devices use strong encryption.
What’s Happening: Some devices send data in plaintext (unencrypted) or use weak encryption algorithms that can be cracked by hackers.
Example: If an insulin pump sends unencrypted data to a doctor’s computer, a hacker could intercept it and alter the dosage instructions, potentially causing harm to the patient.
2. Authentication Protocols
Authentication is how a device verifies that someone (or something) is who they claim to be. Think of it like a password or a fingerprint scan. But many medical IoT devices use weak or default authentication methods.
What’s Happening: Devices might use hardcoded passwords (e.g., “admin” or “1234”) or lack multi-factor authentication (MFA).
Example: A hacker could use a default password to gain access to a hospital’s network of infusion pumps and change their settings, leading to incorrect medication doses.
3. Specific Attack Vectors
Let’s break down how a hacker might exploit a vulnerability in a real-world device, like an insulin pump:
Step 1: Reconnaissance
The hacker scans for vulnerable devices connected to the internet. Many medical IoT devices are discoverable through tools like Shodan, a search engine for connected devices.
Step 2: Exploiting Weak Authentication
The hacker tries default credentials or brute-forces the password to gain access to the insulin pump’s control interface.
Step 3: Intercepting or Altering Data
Once inside, the hacker can intercept data (e.g., blood sugar levels) or send malicious commands (e.g., delivering an incorrect insulin dose).
Step 4: Covering Their Tracks
The hacker might delete logs or use encryption to hide their activity, making it hard for healthcare providers to detect the attack.
This isn’t just theoretical. Researchers have demonstrated these attacks in controlled environments to highlight the risks.
Real-Life Examples That’ll Make You Side-Eye Your Smartwatch
Let’s talk about some real-world incidents that’ll make you go, “Oh no, this is actually happening”:
The St. Jude Medical Hack (2017): Researchers found that certain implantable cardiac devices had vulnerabilities that could let hackers mess with the device’s functionality. Imagine your pacemaker getting hacked and delivering random shocks to your heart. Terrifying, right?
The Hacked Pacemakers (2018): In a chilling demonstration, the FDA confirmed that nearly half a million pacemakers were vulnerable to hacking. Hackers could potentially alter the device’s settings, drain its battery, or even deliver fatal electric shocks. Abbott (the manufacturer) had to issue a firmware update to patch the vulnerability, but not all devices could be updated remotely, leaving some patients at risk.
Ransomware in Hospitals (2020): A ransomware attack on a German hospital disrupted its systems, and a patient who needed urgent care died because the hospital couldn’t operate properly. This wasn’t a direct attack on a medical device, but it shows how vulnerable healthcare systems are.
These aren’t just hypothetical scenarios. They’re happening, and they’re putting lives at risk.
Who’s Behind These Attacks?
Not all hackers are created equal. Here’s who might be targeting medical IoT devices:
Cybercriminals: They’re in it for the money. They might steal patient data to sell on the dark web or lock down hospital systems with ransomware.
Nation-States: Some governments use cyberattacks as a form of espionage or warfare. Targeting medical devices could be a way to destabilize a country or gather intel.
Hacktivists: These are hackers with a cause. They might attack a hospital to make a political statement or expose security flaws.
So… What Can We Do About It?
The good news is that there are ways to protect medical IoT devices. It’s not a lost cause...yet. Here’s what needs to happen:
1. For Manufacturers:
Stop Using Default Passwords: Imagine leaving your front door unlocked with a sign that says, “Welcome, hackers!” That’s what default passwords like “admin” or “1234” do. Manufacturers need to make sure every device has a unique, strong password right out of the box.
Lock Down Data with Strong Encryption: Encryption is like putting your data in a safe. Manufacturers should use the strongest locks available (like AES-256 encryption) to keep patient information safe from prying eyes.
Test for Weak Spots Before Selling Devices: Before releasing a device, manufacturers should hire ethical hackers to try and break into it. This is called penetration testing, and it helps find and fix vulnerabilities before they can be exploited.
Follow the Rules (FDA Guidelines): The FDA has a set of rules for making sure medical devices are secure. Manufacturers need to follow these guidelines to keep patients safe.
2. For Hospitals and Doctors:
Keep Medical Devices on a Separate Network: Think of it like having a VIP section at a concert. Hospitals should keep medical devices on their own secure network, away from the rest of the hospital’s systems. This makes it harder for hackers to sneak in.
Watch for Suspicious Activity: Hospitals should use tools that act like security cameras for their networks. These tools, called intrusion detection systems (IDS), can spot hackers trying to break in and alert the staff.
Train Staff to Spot Cyber Threats: Doctors and nurses are experts at keeping patients healthy, but they might not know much about cybersecurity. Hospitals should train their staff to recognize and respond to cyber threats, like phishing emails or suspicious device behavior.
3. For Patients:
Keep Your Device’s Software Up to Date: Just like you update your phone to get the latest features and security fixes, you should update your medical devices. These updates often include patches for known vulnerabilities.
Avoid Public Wi-Fi: Public Wi-Fi is like shouting your secrets in a crowded room, anyone can listen in. If your medical device connects to the internet, make sure it’s using a secure, private network.
Use a VPN for Extra Security: A VPN is like a secret tunnel for your internet traffic. It keeps your data safe from hackers, especially if you’re accessing medical information remotely.
The Bigger Picture: Why This Matters for Everyone
Okay, so this isn’t just a tech issue. It’s a public health issue. Vulnerable populations, like the elderly, people with chronic illnesses, or those who rely on medical devices to stay alive, are often the most at risk. And let’s be real: it’s not fair that some people are more at risk than others just because of their income or where they live.
Here’s the thing: wealthier patients might have access to the latest, most secure devices or private healthcare, while lower-income patients could be stuck with outdated or less secure options. Imagine needing a pacemaker but only being able to afford one that hasn’t been updated in years and is vulnerable to hacking. That’s not just unfair; it’s dangerous. And it’s something we need to fix as a society.
But it’s not just about money. There’s a bigger ethical responsibility here. Manufacturers need to prioritize patient safety over profits. That means investing in strong encryption, regular updates, and rigorous testing before releasing devices. And governments? They need to step up and enforce stricter cybersecurity standards to hold manufacturers accountable.
And let’s talk about the legal side for a sec. Laws like the FDA’s cybersecurity guidelines and the EU’s Medical Device Regulation are supposed to keep us safe, but they often lag behind the fast pace of tech advancements. Plus, there’s the whole question of liability: if a hacked device harms someone, who’s responsible? The manufacturer? The hospital? The patient? It’s a legal gray area that needs clarity.
Oh, and it’s not just a problem in wealthy countries. In developing nations, where healthcare systems are already stretched thin, a cyberattack on medical devices could be catastrophic. Access to secure healthcare is a basic human right, and we’re failing to protect that right when we ignore these vulnerabilities.
So yeah, this isn’t just about fancy gadgets or tech jargon. It’s about people’s lives. It’s about making sure that everyone, no matter their income or where they live, has access to safe, secure healthcare. And that’s something we all need to care about.
Final Thoughts
Medical IoT devices are a game-changer for healthcare, but their security flaws are a ticking time bomb. We can’t afford to ignore this issue, not when lives are on the line. Whether you’re a patient, a doctor, or just someone who cares about tech and ethics, it’s time to start paying attention.
So, the next time you hear about a smart pacemaker or a glucose-monitoring app, remember: with great tech comes great responsibility.
Further Reading
If you’re as obsessed with this topic as I am, here are some links to dive deeper:
MuddyWater’s Exploitation of Medical Devices (CISA Alert)
FDA Cybersecurity Guidelines for Medical Devices
Shodan: The Search Engine for Connected Devices
European Union Medical Device Regulation (MDR)
TL;DR
Medical IoT devices are amazing but have serious security flaws. Hackers can exploit these flaws to harm patients, and we need better safeguards to prevent this. Everyone (manufacturers, hospitals, and patients) has a role to play in making these devices safer.
2 notes
·
View notes
Text
Best Payment Gateway – Quick Pay
In the fast-paced digital age of today, online payments have become an essential aspect of conducting business. You could be an entrepreneur, a small business proprietor, or running a large corporation; selecting the best payment gateway is necessary to give your customers a seamless, secure, and hassle-free payment experience. That's where Quick Pay comes in—ultimately the best payment gateway solution for streamlining online transactions and giving businesses a trustworthy, hassle-free platform.
What is Quick Pay?
Quick Pay is a modern and trustworthy best payment gateway that allows companies to accept payments from clients around the world. Whether you have an online store, subscription-based business, or sell services online, Quick Pay provides a straightforward and safe means of accepting payments. Its powerful infrastructure and adjustable features make it the best fit for businesses of all shapes and sizes.
Quick Pay is specifically made to enable a wide range of transactions such as credit and debit card transactions, bank transfers, UPI, digital wallets, and many more. Quick Pay, with its rapid processing of transactions and easy-to-use interface, has become one of the top best payment gateways in the present times.
Key Features of Quick Pay
1. Security You Can Trust
One of the most important elements of any internet payment system is security. Quick Pay is serious about security and uses industry-standard encryption to secure customer data. It is PCI DSS (Payment Card Industry Data Security Standard) compliant, indicating that it follows the highest security standards for the protection of cardholder information.
Quick Pay employs SSL encryption to protect all transactions, ensuring your customers' sensitive payment data is safe from fraudsters. It also incorporates two-factor authentication (2FA) and sophisticated fraud detection tools, adding a level of protection to minimize unauthorized transactions. You can be certain that each transaction is secure when you have Quick Pay as your best payment gateway.
2. Seamless Integration
Quick Pay's seamless integration process enables companies to link their online platforms effortlessly, be it an e-commerce site, mobile application, or online reservation platform. With powerful APIs and plugins, integrating Quick Pay into your system is quick and easy.
3. Global Payment Acceptance
For companies interested in going international, Quick Pay has a total solution for taking payment from foreign customers. It's multi-currency enabled, and businesses can sell to customers all over the globe and process payment in the local currency preferred by their customers.
This worldwide coverage positions Quick Pay as a great option for companies that are involved in a global market. You can receive payments from consumers located in other nations, opening your company to more customers, and minimize the trouble of having to deal with several different payment processors. As a world solution, Quick Pay is genuinely the best payment gateway to use for international transactions.
4. Immediate Payment Processing
Quick Pay is built for velocity. Whatever you're charging for a product, service, or subscription, Quick Pay facilitates fast and effective payments. Its real-time payment processing means that businesses get paid in an instant, enabling faster order fulfillment and improved customer experience.
The rapid payment processing also assists in minimizing cart abandonment rates, as the customers will readily complete a transaction when they're assured that it would be processed rapidly and not delayed. Quick Pay facilitates companies to reap the benefits of the finest payment gateway for efficient and rapid payment processing.
5. Customizable Payment Solutions
Each business is different, and Quick Pay knows that one size won't fit all. Whether you require recurring billing for subscriptions, single payments for product sales, or payment solutions specific to your business model, Quick Pay provides a flexible solution.
With adjustable features, companies can tailor payment pages and processes to suit their individual requirements. Quick Pay has both fixed and dynamic pricing support, allowing companies to provide customized pricing plans based on customer preferences or market dynamics. In terms of flexibility, Quick Pay is indeed the most suitable payment gateway for your business requirements.
6. Comprehensive Analytics and Reporting
With Quick Pay, you have access to a rich suite of reporting and analytics tools that give you worthwhile insights into your payment transactions. The dashboard presents you with an uncluttered picture of your transaction history, sales volume, refund history, and much more, helping you keep the financial performance of your business easily in check.
These analytics platforms also assist companies in recognizing trends, tracking customer actions, and handling cash flow in an effective manner, all within a single integrated platform. Your company will always have the information it requires to remain at the top of the game through Quick Pay's reporting and analytics features, which makes it the optimal payment gateway for financial management and business expansion.
7. 24/7 Customer Support
A payment gateway should always offer prompt and reliable customer support, and Quick Pay excels in this area. The platform offers 24/7 customer support via multiple channels, including phone, email, and live chat, ensuring that businesses and customers can resolve any payment-related issues quickly and efficiently. This round-the-clock support ensures that you never have to worry about payment disruptions, giving you peace of mind while running your business. As the best payment gateway, Quick Pay is always available to assist you and your customers.
8. Mobile-Friendly Payment Gateway
With mobile commerce on the rise, a mobile-optimized payment gateway is a must. Quick Pay's mobile-responsive interface makes it possible for customers to make payments effortlessly from any device, be it their desktop, tablet, or smartphone.
The responsive design makes the payment process smooth and easy, irrespective of the device used, which is very important in delivering a great user experience. As a top payment gateway, Quick Pay makes sure that your customers enjoy the best payment experience on any device.
Why Use Quick Pay?
1. Reliability and Uptime
Quick Pay’s robust infrastructure ensures that your business can process payments round the clock, with minimal downtime. The platform guarantees high uptime, which is crucial for businesses that rely on consistent payment processing. When it comes to reliability, Quick Pay is undoubtedly the best payment gateway to keep your business running smoothly.
2. Affordable Pricing Plans
Quick Pay provides affordable and transparent price plans, optimized to suit companies of all sizes. There are no hidden costs, and you pay only for what you utilize, giving you the best returns on your investment. Whether a small business startup or a big enterprise, Quick Pay has pricing plans that can fit your needs, making it an affordable top payment gateway for every business.
3. Customer Trust
With thousands of companies already using Quick Pay for their payment processing requirements, it has established itself as a company that is dependable, secure, and efficient. Quick Pay is used by companies in all sectors, ranging from e-commerce and retail to hospitality and services. This trust is what makes Quick Pay the most suitable payment gateway for your business.
Conclusion
In the current digital economy, an enterprise needs to have a fast, reliable, and secure payment gateway in order to prosper online. Quick Pay is one of the most prominent payment gateways that provides an easy, secure, and convenient platform for making online payments.
With its seamless integration, rapid transaction processing, international presence, and best-in-class security, Quick Pay is the perfect solution for companies looking for a powerful and easy-to-use payment gateway. Whether you're operating a small business or a large corporation, Quick Pay gives you the tools and assistance you require to thrive in the fast-paced arena of online payments.
To learn more and sign up for Quick Pay today, go to Quick Pay.
2 notes
·
View notes
Text

IMSI Catchers Makes SMS Untrusted
IMSI-bitsy little Stinger
The eavesdropping device known as the International Mobile Subscriber Identity- catcher, or IMSI-catcher has rendered the Short Messaging System (SMS or Text) service a veritable sea of peril. These mobile and portable devices which presents a fake mobile phone as a legitimate one to the genuine mobile base station or cell site and at the same time presents a fake base station as a legitimate one to the genuine mobile phone. Lost you there right?
*Would not be delving into the technical details as the interwebz already has a lot of those for your later reference.
Short story - they fake a mobile phone and a cell site and in doing so performs a Man-in-the-middle attack (MITM in Security parlance). They place themselves in-between the phone and the cell site and hence able to intercept and collect information as well as send messages to either parties.
Did i mention that some models can fit in a bag while others in a car? Good luck in chasing much less finding them!
Vanity is my Favorite Sin
The result is utter chaos as the once 'trusted' vanity numbers and names that were sold by Telcos and used by companies can now be copied and presented to the victim. After getting used to these in previous valid interactions, the poor hapless user succumbs to special offers, freebies, account and credential issues and essentially anything that can illicit interest or duress for you to click the accompanying (Phishing/Fake Website) link.
These, along with clever manipulations like telling you that you have exceeded the number of login attempts (regardless of the fact that you entered them correctly), they will initiate an SMS OTP 2FA in the guise of you validating your identity and then capturing these. They then use this to register another device and effectively lock you out and complete the account takeover process - Game Over.
Check the link? Nah.
The URLs in the SMS messages are actually dead giveaways as they are usually not the domains of the legitimate companies, but again you wouldn't think twice as these SMS messages comes from the same vanity number or name that you have been comfortable with as you have been dealing with them in the past.
Bottom line - a LOT of People have now been duped. Luring them to a fake website to initiate the phishing attack and complete the take over process.
Telcos to their credit have disabled links in their SMS service but this is now beyond that as the SMS messages do not even come from them. In the same token, companies who had their vanity numbers mimicked wont be able to recognize if a transaction is fraudulent as the perpetrators already had transferred the credentials to their new device.
Woe is the end-user. What Now?
The obvious way to prevent this is to NEVER CLICK A LINK in an SMS Message EVER. JUST DONT. No IFs and BUTs about it but it's just how it's going to be from now on. Pity the excellent real-time marketing tool and instantaneous notification - You just can't trust SMS/Texting anymore. Now you have to be wary of all SMS messages including Emergency Notifications - May Link ba ito? (Is there a Link here?)
What you know and What You have.. needs more
Tis' the time to add 'What you Are' to the MFA (Multi-factor Authentication) mix permanently and not as an option. Biometrics would have to be added to the mix by DEFAULT or until Mobile communication technology finds a way to create a better mutual authentication and Encryption scheme that cannot be subverted or cracked by the IMSY-bitsy-stingers.
2 notes
·
View notes
Text

Crypto Exchange API Integration: Simplifying and Enhancing Trading Efficiency
The cryptocurrency trading landscape is fast-paced, requiring seamless processes and real-time data access to ensure traders stay ahead of market movements. To meet these demands, Crypto Exchange APIs (Application Programming Interfaces) have emerged as indispensable tools for developers and businesses, streamlining trading processes and improving user experience.
APIs bridge the gap between users, trading platforms, and blockchain networks, enabling efficient operations like order execution, wallet integration, and market data retrieval. This blog dives into the importance of crypto exchange API integration, its benefits, and how businesses can leverage it to create feature-rich trading platforms.
What is a Crypto Exchange API?
A Crypto Exchange API is a software interface that enables seamless communication between cryptocurrency trading platforms and external applications. It provides developers with access to various functionalities, such as real-time price tracking, trade execution, and account management, allowing them to integrate these features into their platforms.
Types of Crypto Exchange APIs:
REST APIs: Used for simple, one-time data requests (e.g., fetching market data or placing a trade).
WebSocket APIs: Provide real-time data streaming for high-frequency trading and live updates.
FIX APIs (Financial Information Exchange): Designed for institutional-grade trading with high-speed data transfers.
Key Benefits of Crypto Exchange API Integration
1. Real-Time Market Data Access
APIs provide up-to-the-second updates on cryptocurrency prices, trading volumes, and order book depth, empowering traders to make informed decisions.
Use Case:
Developers can build dashboards that display live market trends and price movements.
2. Automated Trading
APIs enable algorithmic trading by allowing users to execute buy and sell orders based on predefined conditions.
Use Case:
A trading bot can automatically place orders when specific market criteria are met, eliminating the need for manual intervention.
3. Multi-Exchange Connectivity
Crypto APIs allow platforms to connect with multiple exchanges, aggregating liquidity and providing users with the best trading options.
Use Case:
Traders can access a broader range of cryptocurrencies and trading pairs without switching between platforms.
4. Enhanced User Experience
By integrating APIs, businesses can offer features like secure wallet connections, fast transaction processing, and detailed analytics, improving the overall user experience.
Use Case:
Users can track their portfolio performance in real-time and manage assets directly through the platform.
5. Increased Scalability
API integration allows trading platforms to handle a higher volume of users and transactions efficiently, ensuring smooth operations during peak trading hours.
Use Case:
Exchanges can scale seamlessly to accommodate growth in user demand.
Essential Features of Crypto Exchange API Integration
1. Trading Functionality
APIs must support core trading actions, such as placing market and limit orders, canceling trades, and retrieving order statuses.
2. Wallet Integration
Securely connect wallets for seamless deposits, withdrawals, and balance tracking.
3. Market Data Access
Provide real-time updates on cryptocurrency prices, trading volumes, and historical data for analysis.
4. Account Management
Allow users to manage their accounts, view transaction history, and set preferences through the API.
5. Security Features
Integrate encryption, two-factor authentication (2FA), and API keys to safeguard user data and funds.
Steps to Integrate Crypto Exchange APIs
1. Define Your Requirements
Determine the functionalities you need, such as trading, wallet integration, or market data retrieval.
2. Choose the Right API Provider
Select a provider that aligns with your platform’s requirements. Popular providers include:
Binance API: Known for real-time data and extensive trading options.
Coinbase API: Ideal for wallet integration and payment processing.
Kraken API: Offers advanced trading tools for institutional users.
3. Implement API Integration
Use REST APIs for basic functionalities like fetching market data.
Implement WebSocket APIs for real-time updates and faster trading processes.
4. Test and Optimize
Conduct thorough testing to ensure the API integration performs seamlessly under different scenarios, including high traffic.
5. Launch and Monitor
Deploy the integrated platform and monitor its performance to address any issues promptly.
Challenges in Crypto Exchange API Integration
1. Security Risks
APIs are vulnerable to breaches if not properly secured. Implement robust encryption, authentication, and monitoring tools to mitigate risks.
2. Latency Issues
High latency can disrupt real-time trading. Opt for APIs with low latency to ensure a smooth user experience.
3. Regulatory Compliance
Ensure the integration adheres to KYC (Know Your Customer) and AML (Anti-Money Laundering) regulations.
The Role of Crypto Exchange Platform Development Services
Partnering with a professional crypto exchange platform development service ensures your platform leverages the full potential of API integration.
What Development Services Offer:
Custom API Solutions: Tailored to your platform’s specific needs.
Enhanced Security: Implementing advanced security measures like API key management and encryption.
Real-Time Capabilities: Optimizing APIs for high-speed data transfers and trading.
Regulatory Compliance: Ensuring the platform meets global legal standards.
Scalability: Building infrastructure that grows with your user base and transaction volume.
Real-World Examples of Successful API Integration
1. Binance
Features: Offers REST and WebSocket APIs for real-time market data and trading.
Impact: Enables developers to build high-performance trading bots and analytics tools.
2. Coinbase
Features: Provides secure wallet management APIs and payment processing tools.
Impact: Streamlines crypto payments and wallet integration for businesses.
3. Kraken
Features: Advanced trading APIs for institutional and professional traders.
Impact: Supports multi-currency trading with low-latency data feeds.
Conclusion
Crypto exchange API integration is a game-changer for businesses looking to streamline trading processes and enhance user experience. From enabling real-time data access to automating trades and managing wallets, APIs unlock endless possibilities for innovation in cryptocurrency trading platforms.
By partnering with expert crypto exchange platform development services, you can ensure secure, scalable, and efficient API integration tailored to your platform’s needs. In the ever-evolving world of cryptocurrency, seamless API integration is not just an advantage—it’s a necessity for staying ahead of the competition.
Are you ready to take your crypto exchange platform to the next level?
#cryptocurrencyexchange#crypto exchange platform development company#crypto exchange development company#white label crypto exchange development#cryptocurrency exchange development service#cryptoexchange
2 notes
·
View notes
Text
Top Benefits of Magento over other eCommerce Platforms
Magento is one of the most sought-after e-commerce solutions, with many features that make it stand out from other solutions. Whether a small store or a large enterprise, Magento offers unique benefits to businesses of all sizes.
Reasons why Magento is different?
1. Highly Customizable
Magento is open-source, fully allowing you to have complete control over the functionality, design, and features of your website. This flexibility can enable you to create a truly unique online store that best describes your brand and suits your individual business needs. Magento enables adding any custom extension to tweak the design.
2. Scalability
Unlike many other eCommerce solutions, Magento easily sustains a growing business. It hosts thousands of products and volumes of traffic at high rates, all while still maintaining performance. This makes it an excellent choice for businesses with plans to scale up in the future.
3. Rich Features
Magento is designed with various solid features such as multi-store, advanced inventory management, SEO optimization, and inbuilt marketing options. The above-mentioned features not only smoothen the functions of operation but also give your online business a real visibility boost for easier reach toward customers.
4. SEO-Friendly
Magento is designed to help businesses rank higher on search engines. It offers features like customizable URLs, metadata, sitemaps, and mobile-friendly designs-all of which are important for search engine optimization. That means your store has a better chance of reaching your target audience organically.

5. Integration Options
Magento supports integration with third-party tools and services, including payment gateways, CRMs, ERPs, and shipping providers. This ensures seamless operation and helps improve the overall customer experience.
6. Strong Community Support
Due to the large active community of Magento developers, users, and experts all over the world, Magento will provide tons of resources from troubleshooting to implementing innovation. The community is ever ready with technical advice, and best-practice guidance whenever needed.
7. Mobile-Optimized
In today's mobile-first universe, Magento takes the best care that your store performs seamlessly on everything. Its wide scope of responsive design contributes much to a better buying experience for any end-user on devices with smaller features than desktops, or basically, all types of phones and tablets-and improve conversions significantly.
8. Security
Magento is designed to offer the best in terms of security, including data encryption, two-factor authentication, and regular updates. This ensures your online store is protected against cyber threats.
With Magento, your business will be able to grow and thrive in today's competitive eCommerce landscape because of its flexibility, scalability, and rich features. SEO-friendly, with strong community support, it's a platform that will help you reach long-term success.
2 notes
·
View notes
Text
What Are the Costs Associated with Fintech Software Development?

The fintech industry is experiencing exponential growth, driven by advancements in technology and increasing demand for innovative financial solutions. As organizations look to capitalize on this trend, understanding the costs associated with fintech software development becomes crucial. Developing robust and secure applications, especially for fintech payment solutions, requires significant investment in technology, expertise, and compliance measures. This article breaks down the key cost factors involved in fintech software development and how businesses can navigate these expenses effectively.
1. Development Team and Expertise
The development team is one of the most significant cost drivers in fintech software development. Hiring skilled professionals, such as software engineers, UI/UX designers, quality assurance specialists, and project managers, requires a substantial budget. The costs can vary depending on the team’s location, expertise, and experience level. For example:
In-house teams: Employing full-time staff provides better control but comes with recurring costs such as salaries, benefits, and training.
Outsourcing: Hiring external agencies or freelancers can reduce costs, especially if the development team is located in regions with lower labor costs.
2. Technology Stack
The choice of technology stack plays a significant role in the overall development cost. Building secure and scalable fintech payment solutions requires advanced tools, frameworks, and programming languages. Costs include:
Licenses and subscriptions: Some technologies require paid licenses or annual subscriptions.
Infrastructure: Cloud services, databases, and servers are essential for hosting and managing fintech applications.
Integration tools: APIs for payment processing, identity verification, and other functionalities often come with usage fees.
3. Security and Compliance
The fintech industry is heavily regulated, requiring adherence to strict security standards and legal compliance. Implementing these measures adds to the development cost but is essential to avoid potential fines and reputational damage. Key considerations include:
Data encryption: Robust encryption protocols like AES-256 to protect sensitive data.
Compliance certifications: Obtaining certifications such as PCI DSS, GDPR, and ISO/IEC 27001 can be costly but are mandatory for operating in many regions.
Security audits: Regular penetration testing and vulnerability assessments are necessary to ensure application security.
4. Customization and Features
The complexity of the application directly impacts the cost. Basic fintech solutions may have limited functionality, while advanced applications require more extensive development efforts. Common features that add to the cost include:
User authentication: Multi-factor authentication (MFA) and biometric verification.
Real-time processing: Handling high volumes of transactions with minimal latency.
Analytics and reporting: Providing users with detailed financial insights and dashboards.
Blockchain integration: Leveraging blockchain for enhanced security and transparency.
5. User Experience (UX) and Design
A seamless and intuitive user interface is critical for customer retention in the fintech industry. Investing in high-quality UI/UX design ensures that users can navigate the platform effortlessly. Costs in this category include:
Prototyping and wireframing.
Usability testing.
Responsive design for compatibility across devices.
6. Maintenance and Updates
Fintech applications require ongoing maintenance to remain secure and functional. Post-launch costs include:
Bug fixes and updates: Addressing issues and releasing new features.
Server costs: Maintaining and scaling infrastructure to accommodate user growth.
Monitoring tools: Real-time monitoring systems to track performance and security.
7. Marketing and Customer Acquisition
Once the fintech solution is developed, promoting it to the target audience incurs additional costs. Marketing strategies such as digital advertising, influencer partnerships, and content marketing require significant investment. Moreover, onboarding users and providing customer support also contribute to the total cost.
8. Geographic Factors
The cost of fintech software development varies significantly based on geographic factors. Development in North America and Western Europe tends to be more expensive compared to regions like Eastern Europe, South Asia, or Latin America. Businesses must weigh the trade-offs between cost savings and access to high-quality talent.
9. Partnering with Technology Providers
Collaborating with established technology providers can reduce development costs while ensuring top-notch quality. For instance, Xettle Technologies offers comprehensive fintech solutions, including secure APIs and compliance-ready tools, enabling businesses to streamline development processes and minimize risks. Partnering with such providers can save time and resources while enhancing the application's reliability.
Cost Estimates
While costs vary depending on the project's complexity, here are rough estimates:
Basic applications: $50,000 to $100,000.
Moderately complex solutions: $100,000 to $250,000.
Highly advanced platforms: $250,000 and above.
These figures include development, security measures, and initial marketing efforts but may rise with added features or broader scope.
Conclusion
Understanding the costs associated with fintech software development is vital for effective budgeting and project planning. From assembling a skilled team to ensuring compliance and security, each component contributes to the total investment. By leveraging advanced tools and partnering with experienced providers like Xettle Technologies, businesses can optimize costs while delivering high-quality fintech payment solutions. The investment, though significant, lays the foundation for long-term success in the competitive fintech industry.
2 notes
·
View notes
Text
Credit Card Payment Gateway Innovations: Enhancing E-Commerce Platforms
Article by Jonathan Bomser | CEO | Accept-credit-cards-now.com

In today's rapidly changing e-commerce landscape, the ability to process payments efficiently is the cornerstone of online business success. Credit card payment gateways have emerged as the driving force behind these seamless transaction experiences. As technology continues to advance, innovative payment gateway solutions are making waves, transforming how businesses handle credit card transactions and manage financial processes. In this article, we embark on a journey to explore the latest trends and cutting-edge developments in credit card payment gateways. We'll uncover how these innovations are shaping e-commerce platforms to cater to diverse needs, including high-risk transactions, credit repair services, and the CBD industry.
DOWNLOAD THE CREDIT CARD PAYMENT GATEWAY INFOGRAPHICS HERE
Revolutionizing Payment Processing for High-Risk Ventures Businesses operating in high-risk sectors, such as gaming, adult entertainment, or travel, often face significant challenges when it comes to conventional payment processing solutions. The answer to these challenges lies in the form of high-risk merchant accounts and specialized payment gateways. These tailor-made solutions go beyond ensuring secure transactions; they also provide a suite of risk management tools to shield businesses against fraud and other threats.
Empowering E-Commerce with Seamless Payment Solutions The rise of e-commerce has fundamentally transformed how we shop, and credit card payment gateways are pivotal in shaping this transformation. By enabling online credit card payments, businesses can provide their customers with a convenient and efficient checkout experience. Modern payment gateways offer a range of options, including the acceptance of credit and debit card payments, ensuring that customers can choose their preferred payment method.
Supporting the Credit Repair Industry Credit repair companies play a crucial role in helping individuals improve their credit scores and financial well-being. To cater to the unique payment needs of this sector, specialized merchant processing and payment gateway solutions have emerged. These solutions not only ensure secure credit repair payment processing but also seamlessly integrate with credit repair service platforms.
Navigating the Complexities of CBD Payment Processing The burgeoning CBD industry, while experiencing exponential growth, grapples with its high-risk status and intricate regulatory landscape. CBD merchants can now leverage specialized high-risk CBD payment processing solutions, meticulously tailored to meet the exacting demands of their industry. These solutions ensure stringent compliance with regulations while providing a frictionless payment experience for customers.
Innovative Strides in Payment Gateway Solutions Innovative payment gateway providers continuously enhance their services to meet the dynamic needs of contemporary e-commerce. Advanced features like tokenization for secure card storage, multi-currency support, and subscription billing have become commonplace. These features not only streamline payment processes but also cultivate customer trust and loyalty.
Prioritizing Data Security in Payment Gateways Data security remains a paramount concern for both businesses and customers engaging in online transactions. Leading payment gateways prioritize data security by implementing robust encryption, adhering to the Payment Card Industry Data Security Standard (PCI DSS), and integrating two-factor authentication. These measures instill confidence in customers, encouraging them to conduct more online transactions.
youtube
A Unified Approach: Comprehensive Credit Card Payment Services Many payment gateway providers now offer a comprehensive suite of services beyond payment processing. These services may encompass fraud prevention tools, in-depth analytics and reporting, and seamless integrations with other e-commerce tools. By adopting this unified approach, businesses can streamline their operations and provide customers with a seamless and satisfying online experience.
In an era where e-commerce reigns supreme, credit card payment gateways are evolving incessantly to harmonize with the shifting landscape. From the intricate domain of high-risk industries to the specialized realm of credit repair services and the ever-burgeoning horizon of CBD merchants, pioneering payment processing solutions are driving growth and setting new standards for online transactions. By embracing these innovations and selecting the right payment gateway partner, businesses can unlock new avenues of success in the digital realm.
#credit card payment#credit card processing#high risk merchant account#high risk payment gateway#high risk payment processing#merchant processing#payment processing#accept credit cards#Youtube
21 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text
Crypto trading mobile app
Designing a Crypto Trading Mobile App involves a balance of usability, security, and aesthetic appeal, tailored to meet the needs of a fast-paced, data-driven audience. Below is an overview of key components and considerations to craft a seamless and user-centric experience for crypto traders.
Key Elements of a Crypto Trading Mobile App Design
1. Intuitive Onboarding
First Impressions: The onboarding process should be simple, guiding users smoothly from downloading the app to making their first trade.
Account Creation: Offer multiple sign-up options (email, phone number, Google/Apple login) and include KYC (Know Your Customer) verification seamlessly.
Interactive Tutorials: For new traders, provide interactive walkthroughs to explain key features like trading pairs, order placement, and wallet setup.
2. Dashboard & Home Screen
Clean Layout: Display an overview of the user's portfolio, including current balances, market trends, and quick access to popular trading pairs.
Market Overview: Real-time market data should be clearly visible. Include options for users to view coin performance, historical charts, and news snippets.
Customization: Let users customize their dashboard by adding favorite assets or widgets like price alerts, trading volumes, and news feeds.
3. Trading Interface
Simple vs. Advanced Modes: Provide two versions of the trading interface. A simple mode for beginners with basic buy/sell options, and an advanced mode with tools like limit orders, stop losses, and technical indicators.
Charting Tools: Integrate interactive, real-time charts powered by TradingView or similar APIs, allowing users to analyze market movements with tools like candlestick patterns, RSI, and moving averages.
Order Placement: Streamline the process of placing market, limit, and stop orders. Use clear buttons and a concise form layout to minimize errors.
Real-Time Data: Update market prices, balances, and order statuses in real-time. Include a status bar that shows successful or pending trades.
4. Wallet & Portfolio Management
Asset Overview: Provide an easy-to-read portfolio page where users can view all their holdings, including balances, performance (gains/losses), and allocation percentages.
Multi-Currency Support: Display a comprehensive list of supported cryptocurrencies. Enable users to transfer between wallets, send/receive assets, and generate QR codes for transactions.
Transaction History: Offer a detailed transaction history, including dates, amounts, and transaction IDs for transparency and record-keeping.
5. Security Features
Biometric Authentication: Use fingerprint, facial recognition, or PIN codes for secure logins and transaction confirmations.
Two-Factor Authentication (2FA): Strong security protocols like 2FA with Google Authenticator or SMS verification should be mandatory for withdrawals and sensitive actions.
Push Notifications for Security Alerts: Keep users informed about logins from new devices, suspicious activities, or price movements via push notifications.
6. User-Friendly Navigation
Bottom Navigation Bar: Include key sections like Home, Markets, Wallet, Trade, and Settings. The icons should be simple, recognizable, and easily accessible with one hand.
Search Bar: A prominent search feature to quickly locate specific coins, trading pairs, or help topics.
7. Analytics & Insights
Market Trends: Display comprehensive analytics including top gainers, losers, and market sentiment indicators.
Push Alerts for Price Movements: Offer customizable price alert notifications to help users react quickly to market changes.
Educational Content: Include sections with tips on technical analysis, crypto market basics, or new coin listings.
8. Social and Community Features
Live Chat: Provide a feature for users to chat with customer support or engage with other traders in a community setting.
News Feed: Integrate crypto news from trusted sources to keep users updated with the latest market-moving events.
9. Light and Dark Mode
Themes: Offer both light and dark mode to cater to users who trade at different times of day. The dark mode is especially important for night traders to reduce eye strain.
10. Settings and Customization
Personalization Options: Allow users to choose preferred currencies, set trading limits, and configure alerts based on their personal preferences.
Language and Regional Settings: Provide multilingual support and regional settings for global users.
Visual Design Considerations
Modern, Minimalist Design: A clean, minimal UI is essential for avoiding clutter, especially when dealing with complex data like market trends and charts.
Color Scheme: Use a professional color palette with accents for call-to-action buttons. Green and red are typically used for indicating gains and losses, respectively.
Animations & Micro-interactions: Subtle animations can enhance the experience by providing feedback on button presses or transitions between screens. However, keep these minimal to avoid slowing down performance.
Conclusion
Designing a crypto trading mobile app requires focusing on accessibility, performance, and security. By blending these elements with a modern, intuitive interface and robust features, your app can empower users to navigate the fast-paced world of crypto trading with confidence and ease.
#uxbridge#uxuidesign#ui ux development services#ux design services#ux research#ux tools#ui ux agency#ux#uxinspiration#ui ux development company#crypto#blockchain#defi#ethereum#altcoin#fintech
2 notes
·
View notes